🔒 Creating and Managing a Custom Banned Password List in Entra ID
Weak and commonly used passwords remain one of the most exploited vulnerabilities in modern identity systems. To mitigate this, Entra ID (formerly Azure Active Directory) provides administrators with the ability to enforce custom banned password lists, supplementing Microsoft ’s global banned password list. This guide explains the importance of this feature, how to use it effectively, and step-by-step setup instructions using Entra Admin Centre .
🔐 Why Use a Custom Banned Password List?
Microsoft already maintains a global banned password list that blocks over 2,000 commonly used and easily guessable passwords. However, attackers often tailor their password-guessing strategies to specific organisations, using company names, locations, and predictable patterns.
By implementing a custom banned password list, you can:
- Prevent use of organisational terms (eg. company name, locations, project names)
- Block common variants (eg.
[CompanyName]123,Welcome2024,Password!) - Strengthen your password policy beyond the generic protections
🛠️ Setting Up a Custom Banned Password List (via Entra Admin Centre)
Pre-requisites: You need Microsoft Entra ID P1 or P2 licensing.
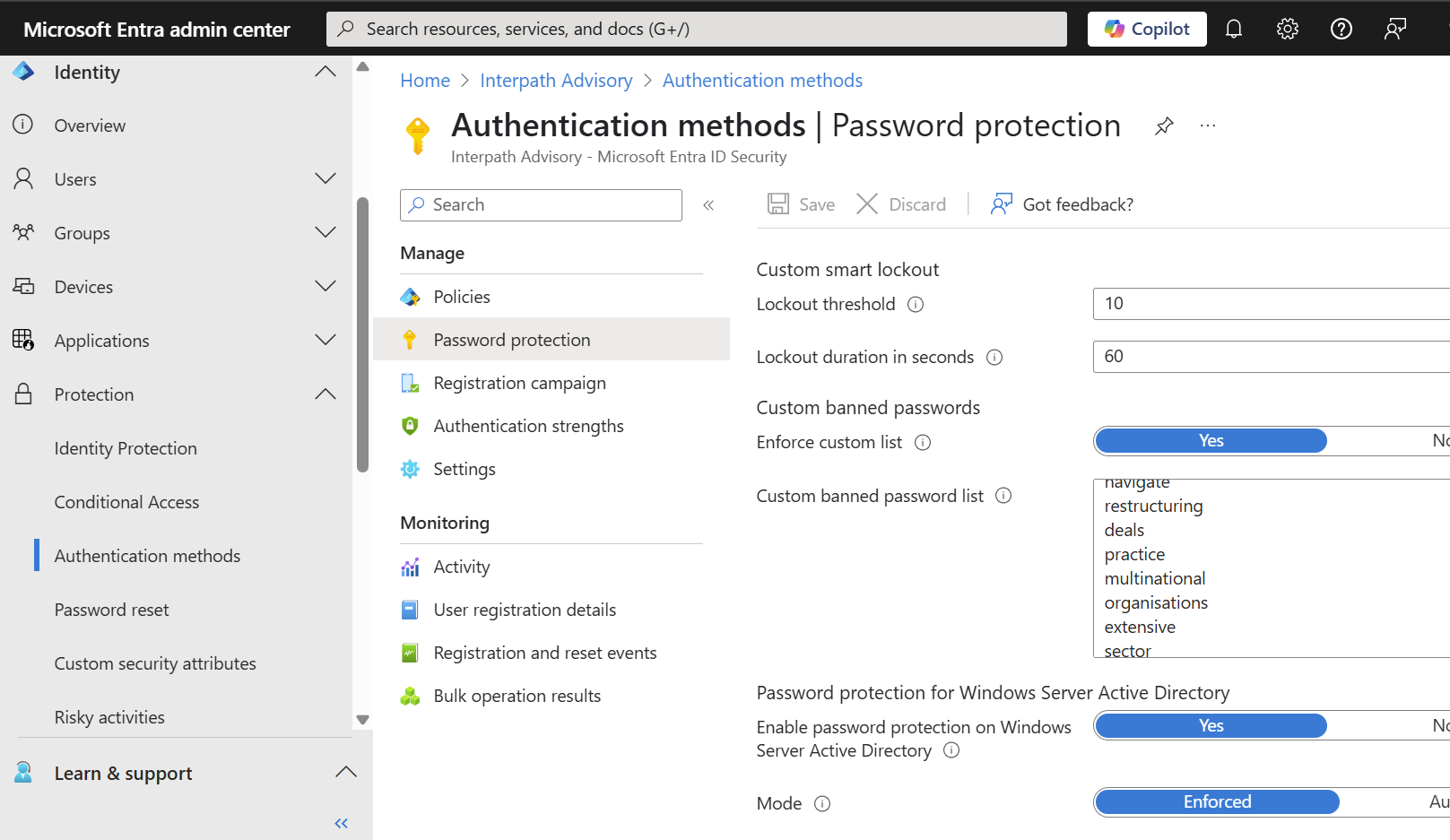
01: Access Authentication Methods
- Go to the Microsoft - Entra Admin Center
- Navigate to:
Protection > Authentication methods > Password protection
02: Configure Custom Banned Passwords
- Under Custom banned passwords, toggle Enable to Yes
- In the Custom banned password list, add up to 1,000 terms, one per line
- Click Save
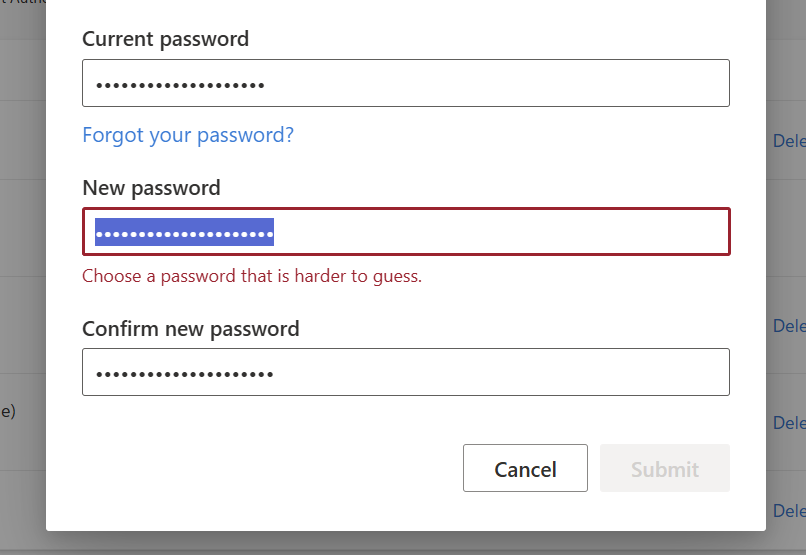
Once configured, no matter how complex the password is, if it includes any words from the banned password list, you will be prompted to choose a password that is harder to guess, as shown below.
Tip: Include variations or misspellings of organisational terms (eg. mycompany, mycompany1, myc0mpany).
Best Practices :
- Avoid actual passwords in the list. Instead, focus on patterns and terms
- Regularly review and update the list as new patterns emerge
- Combine with smart lockout, MFA, risk-based policies for maximum protection
| Feature | Description |
|---|---|
| Max custom terms | 1,000 |
| Included in | Azure AD Premium P1/P2 |
| Applies to | Cloud and hybrid users |
| Configurable via | Portal or PowerShell |
Implementing a custom banned password list is a simple but powerful way to bolster your organisation’s password hygiene and defend against credential-based attacks.